Honeypot-project

My Honeypot Project
My Honeypot project was originally planned as a funny side project together with the group called Zero of the #White-Hat-Hackers Discord, but I ended up doing it solo.
The Idea
A user on Reddit named u/Front-Buyer3535 created three posts in the r/cyber-security subreddit about his project, which rotated login banners on each port to successfully drive bots insane.
Post1 | Post2 | Post3
What happened in 3 months?
- I got 9 abuses with the fact that I have malware hosted on my servers.
- I received more than 500 emails from BSI with a warning that my critical
services are looking outside
- I collected more than 120 thousand IP addresses that are constantly scanning my
servers
- Censys and Shodan stopped scanning my servers :D
The Plan
First, I had to find a suitable piece of software that I could modify to fit my needs and run on a brain-dead 1-core, 1 GiB RAM VPS. Bonus points if the host offered multiple ports to connect to. So I did what I do best — googled around, annoyed people with questions on various Discords (<3 #KiraSec), and ruined several VMs in my homelab.
~ TPOT (https://github.com/telekom-security/tpotce)
T-Pot is the all in one, optionally distributed, multiarch (amd64,
arm64) honeypot plattform, supporting 20+ honeypots and countless visualization
options using the Elastic Stack, animated live attack maps and lots of security
tools to further improve the deception experience.
Fine, fine, fine — I thought at first, until I saw the system requirements (8GB RAM, 128GB SSD for the sensors).
Yes, yes, I know that you can run each external service individually and configure TPOT — but my goal was something simple, something I could easily modify... so: NEXT.
~ QeeqBox Honeypots (https://github.com/qeeqbox/honeypots)
30 low-high level honeypots in a single PyPI package for monitoring network
traffic, bots activities, and username \ password credentials.
A pretty interesting project, which is apparently also integrated into TPOT — so it can’t be that bad, right? Sadly, it turned out to be too resource-hungry for my low-spec setup, so I ditched it as well.
~ Heralding (https://github.com/johnnykv/heralding)
Sometimes you just want a simple honeypot that collects credentials, nothing more.
Heralding is that honeypot! Currently the following protocols are supported: ftp,
telnet, ssh, http, https, pop3, pop3s, imap, imaps, smtp, vnc, postgresql and
socks5.This description - this can be only a checkpot right? Setting it up turned out to be super extra easy. GUIDE(https://github.com/johnnykv/heralding/blob/master/INSTALL.md)
Filling the Pot with Honey
Following the guide turned out to be pretty easy. Create Venv, install dependencies, write config into heralding.yml - start - works - fine.
I wont do a full walkthrough on the installation at this point, because it is really dirt easy. RTFM https://github.com/johnnykv/heralding/blob/master/INSTALL.md
While i was setting up the pots on Sensor A (thats how i named the honey pot host), i got already scanned by censys. This can only work.
The Backend
Ok, we got the honey in the pot but what to do with the data i gained?
To be honest, i dont trust Heralding entirely. Its dependencies are outdated and it is under handling by 22 different people. I wanted a database and grafana to be independent, so i can simply restore a snapshot if something feels fishy.
I set up a second VPS and wrote a simple webserver, that will receive the data from the honey pot via POST Request and pastes it into a database.
I wrote a simple autorisation system, setup a whitelist and implemented a soft ratelimit, just in case.
If you are interested in this, contact me and i will make a second blogpost out of it.
I modified the log handling of heralding, to forward the logs to my webserver instead of writing it into a .csv file.
The Result looks like that:
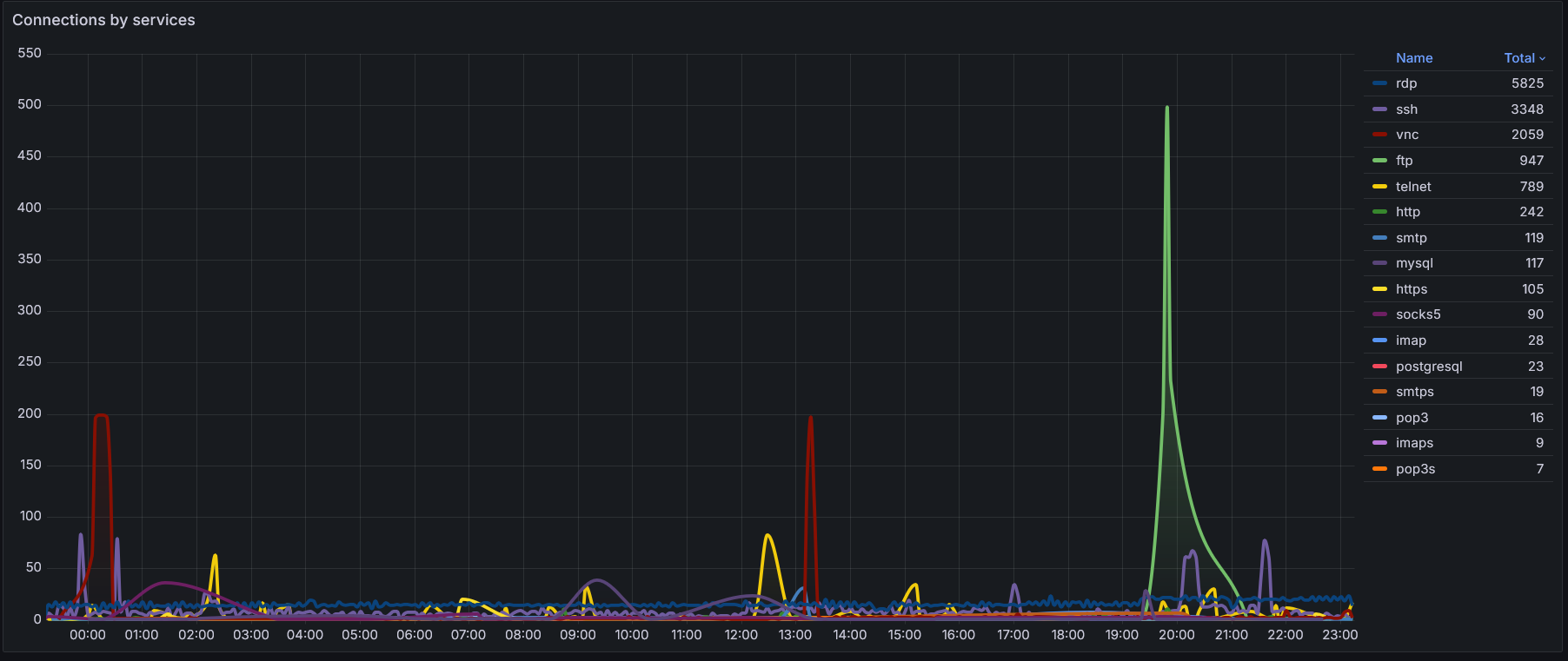
Public Grafana Board: https://grafana.8391nn32.xyz/public-dashboards/7c648a53754e4206b410f5590afd8ec2
Current State
I reported the top 30 scanners to their service providers abuse address, only one (hetzner) responded.
Total Connection attempts 15.236
o7
Tags: #honeypot #homeproject